hi everyone! long time no see. the job (TM) takes up a lot of time and mental energy and so does trying to make it work with everything else going on in my life.
i’ll be uploading a bunch of stuff i’ve been working on on the side soon. something something being raised a woman, something something being aware that there are people you would rather not read your shit who are going to read your shit so long as you publish it, something something opsec. smh.
anyways, please enjoy my now approved final thesis proposal for my first masters.
Prepositioning and persistence in cyberspace: a longitudinal model for adversary behaviour
1. Introduction
This thesis aims at clarifying the concepts of prepositioning and persistence as pertains to cyberspace. These terms are used with varying meanings, some more or less appropriate, and tacked onto various theories and models of international relations in cyberspace. This lack of conceptual clarity obfuscates some of the implications that will hopefully emerge from the distinction presented in this work.
In the first place, we will provide a working definition of the two concepts of prepositioning and persistence: prepositioning refers to adversarial presence on a system without exploitation, while persistence refers to adversarial exploitation of a system. We will then explain how centering the longitudinal dimension of time is key, in agreement with part of the literature that argues the cyber domain has broadly moved beyond deterrence.
The thesis then focuses on exploring a series of case studies that stretch the definition of malicious cyber activity in various ways. This has two functions: on the one hand it allows us to test the validity and completeness of the model proposed above; and on the other, to see if applying this model gives us any further insight on these case studies.
While popular discussion often refers to “cyberattacks” as single events, offensive activity in cyberspace is often not punctiform: they are often closer to marathons than to sprints. As will be shown through the six case studies presented in this thesis, this is particularly true of advanced actors, such as those that tend to assume relevance in international relations.
In the cybersecurity industry, such actors are generally termed “APTs”, for “Advanced Persistent Threats”. While the definition of a threat is clear, and the level of advancement can only be assessed relative to a target, there is not a clear definition of what “persistent” can mean.
For the purposes of this thesis, we will now look into defining the concepts of prepositioning and persistence in relation to the timeline of adversarial conduct in cyberspace. This is the proposed model that will then be tested in the rest of the thesis, with a variety of situations, threats and environments.
It is important to establish that this work is done from a defenders’ perspective. This means that threats that are forever undetected, and thus unknown to the defenders at all points in time, are not part of this framework. Indeed, it is the defenders that attribute prepositioning and persistence to an adversary’s behaviour; an action that can only happen from detection going forward.
In part 3.2 we will look at a series of scenarios first under the hypothesis that the defenders, upon detections, achieve a perfect information picture; and then in part 3.3. under the hypothesis that detection is imperfect and it misses some relevant information. Such scenarios will be termed as “P” scenarios if under the assumption of perfect information, and “I” scenarios if under the assumption of imperfect information.
1.1. Methods
This thesis will be based on:
· Literature, where applicable
· Technical documentation, where public
· Informal discussions with experts (formal interviews will probably be hard to conduct: it’s hard to ensure expert availability)
It will not be possible to attribute some of the innovative framework-building elements of this thesis to external sources. However, this does not mean it is informed by non-public information. In particular, neither this document nor the final thesis are in any way representative of NATO positions.
2. Literature review Why this matters
As we have established in the literature review, actors’ behaviour in cyberspace is no longer just a technical issue; it has vast international political and legal implications. For this reason, it is critical to understand the difference between prepositioning and persistence, as well as their differing consequences and implications. The model proposed above is an attempt to propose a more structured understanding of these issues, and the following part of this thesis will attempt to apply this model to a series of disparate cases, aiming to ensure its validity in a variety of circumstances.
For instance, if a nation-state adversary is caught (detected) prepositioning in a critical infrastructure system or network, it would be reasonable to assume it wants to establish a foothold in such infrastructure to facilitate disruptive or destructive actions in the future, or to surveil and exfiltrate data related to the workings of such infrastructure; or, assuming an imperfect information environment, that it may already have exfiltrated information (successful disruptive and destructive activity is significantly easier to detect). These actions, if attributed to a nation-state, are all indicative of political planning and can significantly impact relations between the adversary and the target. On the other hand, persistence on a system can give an adversary continuous access to nonpublic information. This is most closely comparable to traditional espionage activity, which is not illicit under international law but is consistently criminalised by target nations. In this sense, the ability to establish strong persistence may lead to an informational edge.
3. The proposed longitudinal model for prepositioning and persistence
3.1. Definitions
In order to ensure the utmost possible clarity of the scenarios we will discuss in parts 3.2 and 3.3, we will here provide definitions for the terms (excluding prepositioning and persistence) that will be used to outline the lifecycle of adversarial activity in a network or system.
Adversarial activity
Initial compromise
Exploitation
Detection
Eradication
3.2. Perfect information hypothesis
3.2.1. Scenario P1: Adversarial presence is detected before exploitation occurs
Under a perfect information hypothesis, we propose that prepositioning refers to continued adversarial presence on a system before exploitation.
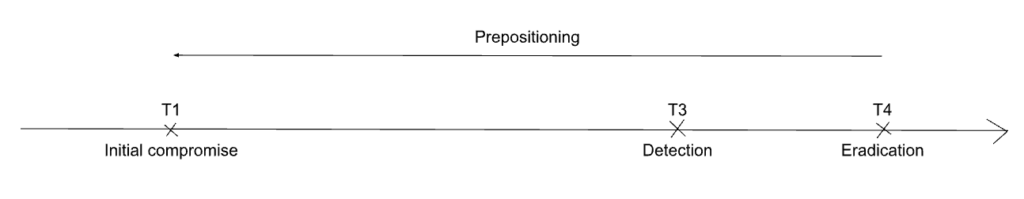
In the graphic above, it is the time between T1 and T4.
In this scenario, upon detecting the adversary’s presence (T3), the defenders are able to positively ascertain that no exploitation has occurred. Thus, they will call the adversary’s presence “prepositioning”. This prepositioning then ends once the defenders are able to definitively eradicate the adversary from the system or network, removing its presence.
3.2.2. Scenario P2: Adversarial presence is detected alongside ongoing exploitation
Under a perfect information hypothesis, we propose that persistence refers to continued adversarial presence on a system accompanied by exploitation.
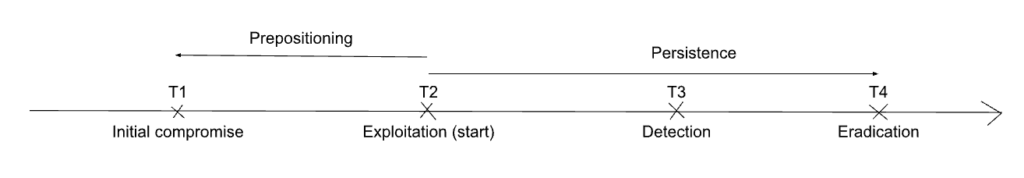
In the graphic above, it is the time between T2 and T4.
In this scenario, the defenders have perfect visibility on the adversary’s past actions. They are able to establish when the initial compromise occurred (T1), and, in case there was a significant wait between that first compromise and the start of the adversary’s exploitation of the system or network (T2), they are able to ascertain the length of this time, which they will term adversary prepositioning. They are able to determine when the exploitation started (T2), which is the starting point of what they can call adversary persistence in the system or network. This persistence ends once the defenders are able to definitively eradicate the adversary from the system or network, removing its presence.
3.2.3. Scenario P3: Adversarial presence is detected after exploitation has concluded
It is possible that the detection happens when the adversary is not actively exploiting the network or system, but after a contained period of time when exploitation has happened. Under a perfect information hypothesis, the situation is as described in the figure below.
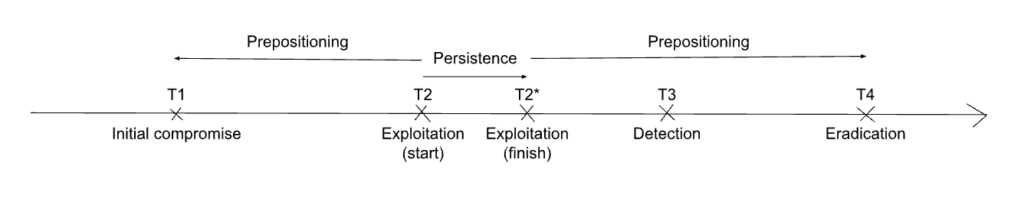
3.3. Imperfect information hypothesis
3.3.1. Scenario I1: Presence is detected, but exploitation is not
Under an imperfect information hypothesis, defenders may detect an adversary’s presence in the system or network without detecting any exploitation.
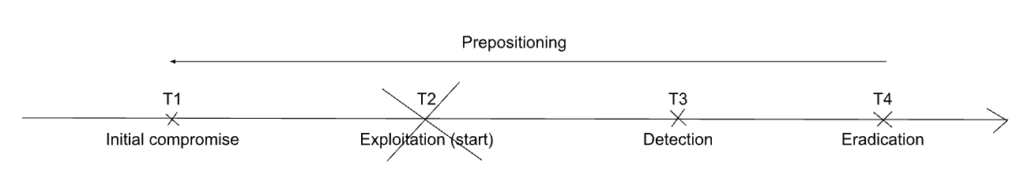
This means that defenders will interpret this as if it was P1, and understand the actor’s behaviour as prepositioning; meanwhile, the actual conduct was the same as P2.
The same can also happen in case the exploitation has already concluded:
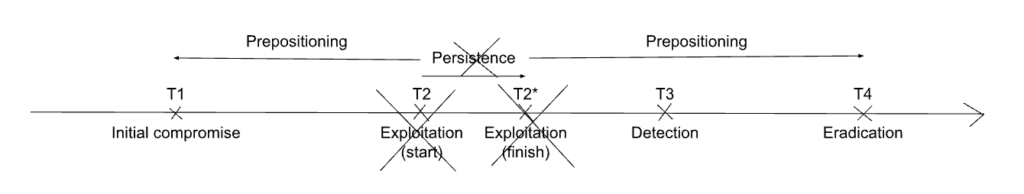
In practice, this means that when the prepositioning of an adversary in a system is detected, it is often deduced that this was in preparation for a later exploitation, which detection and later eradication have thwarted. However, it is possible that cases are classified as prepositioning out of ignorance of the persistent exploitation previous or ongoing.
3.3.2. Scenario I2: Exploitation is detected, but prepositioning is not
The below figure illustrates what happens when the exploitation is detected, but prepositioning is not.
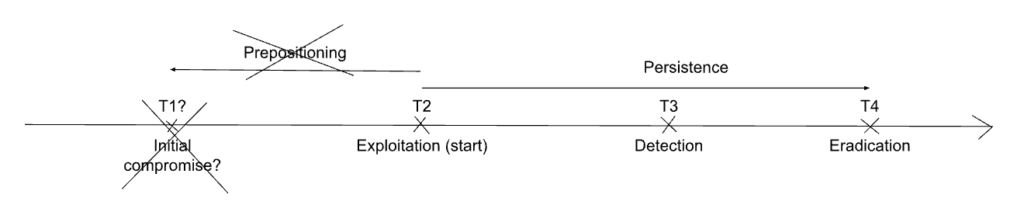
In this scenario, the actor had established presence at some point that was significantly distinct from when it started exploitation. However, the defenders are not aware of this fact, and they believe the adversary established themselves in the network or system at T2.
3.3.3. Scenario I3: Eradication is not complete
This scenario focuses on the final stage of the timeline we have been considering. For this scenario, the first stages of the process are irrelevant; anything before T4 has no material incidence on this hypothetical.
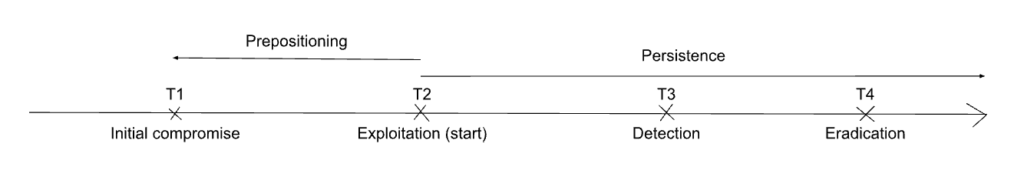
In this case, the defenders are convinced that their actions have eradicated the actor’s presence on the system or network, but this is not the case. In this scenario, the adversary maintains persistence on the network after T4, until and unless another successful eradication attempt or the adversary voluntarily exits the system or network.
3.3.4. Scenario I4: No detection happens
This final scenario is the one where the role of imperfect information reaches its peak. Indeed, the defenders in this scenario are unaware that any adversarial activity has happened on the system at all.
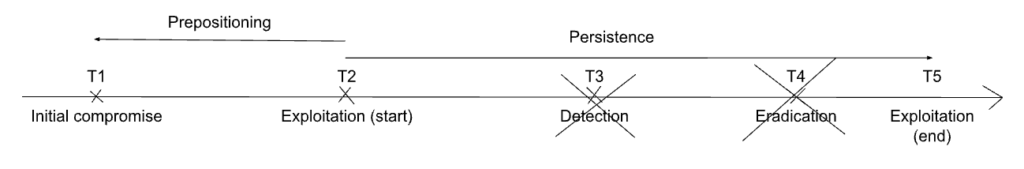
In this scenario, the adversary may or may not exhibit prepositioning, depending on whether a significant amount of time passes between initial compromise and the start of exploitation. From then on, the adversary persists on the network, undetected; no eradication attempts may take place. The exploitation ends either when the adversary decides to leave the system or network upon completion of its mission, or when the system or network is decommissioned.
4. Testing the model: case studies
The purpose of this section is to provide a series of case studies that stretch the definition of malicious cyber activity in various ways. This has two functions: on the one hand it allows us to test the validity and completeness of the model proposed above; and on the other, to see if applying this model gives us any further insight on these case studies.
4.1. Case study: Volt Typhoon
Vague but extremely urgent warnings from highly reputable sources. The warnings concern the fact that actors affiliated with China were detected in the networks of some critical civilian infrastructures in the US. While the US and partner nations have publicly attributed this conduct to China, the amount of public information on this actor and their actions remains limited – probably to maintain visibility into this actor’s techniques and goals.
4.2. Case study: Salt Typhoon
Threat actor associated with China who had achieved persistent access to some US ISPs and to tools used for court-mandated communications wiretapping.
4.3. Case study: undersea communications cables
A case study to look at the physical layer of critical communication infrastructure (extensive bibliography at the ready). Threat model including both physical tapping (data exfiltration) and disruption.
4.4. Case study: Hezbollah’s exploding pagers
Controversial example, far from the “usual cyberattacks”. Was it a cyber attack? No, because it wasn’t achieved by cyber means, but rather by kinetic ones. However, it did impact communications for a party in armed combat, i.e. cyber as a supporting function in warfare. Further, this case study gives us the possibility to highlight the issue of supply chain security; reference to the disputed Super Micro story.
4.5. Case study: New IP and Internet protocol standardisation
Discussion of this case as an unconventional way (standardisation procedures) to attain low-level persistence (influencing in fact the very terrain of the cyber domain). Similarities to supply chains incidents, but much lower visibility (meaning lower risk to reward ratio). (See ESIL Conference presentation; conference paper to be published soon).
5. Conclusions.
4.1. Observations on the model
Reflection on all the above and on the application of this model to the case studies outlined.
4.2. Prepositioning, persistence and deterrence
Cyber deterrence can mean two things: deterring actors from conducting malicious cyber activities, or utilising telegraphed cyber capabilities as part of broader deterrence efforts.
Deterring threat actors from conducting cyber operations is mostly done through imposing costs. However, it’s not the primary mode of interaction in cyberspace at this point, given the opportunistic nature of the attacks that are conducted in it for the most part.
Prepositioning and persistence in adversary systems both have the goal of stealth. However, in case they are found out, it can signal their capabilities, which may ultimately become part of a broader deterrence effort.
4.3. Cyber as an entirely constructed domain
If cyberspace is not just an enabler of other domains and an emergent property of physical infrastructure, but a domain on its own, it is important to look at issues such as these that concern its terrain, as misrepresentations and misunderstandings in this regard may well have a crucial impact in the future.
Some references
Fischerkeller, Michael P. ‘A Cyber Persistence Way to Countermeasures’. Default (blog), 13 February 2023. https://www.lawfaremedia.org/article/cyber-persistence-way-countermeasures.
———. ‘Preparing for a Post-Armed Conflict Strategic Environment’, n.d.
Fischerkeller, Michael P, and Richard J Harknett. ‘Persistent Engagement, Agreed Competition, and Cyberspace Interaction Dynamics and Escalation’, n.d.
Lockheed Martin. ‘Cyber Kill Chain®’. Lockheed Martin. Accessed 15 August 2024. https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html.
Leave a Reply